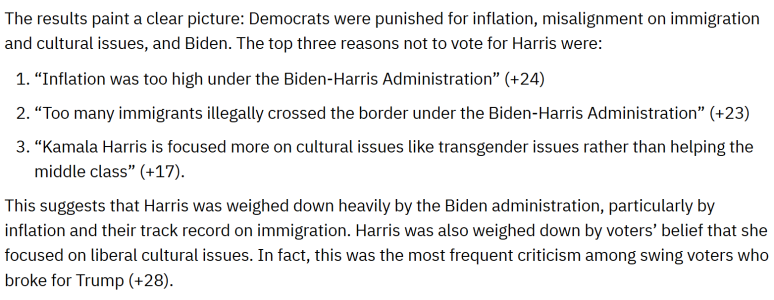
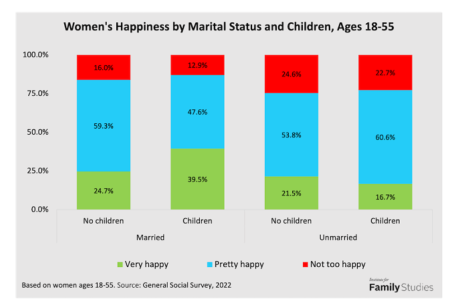
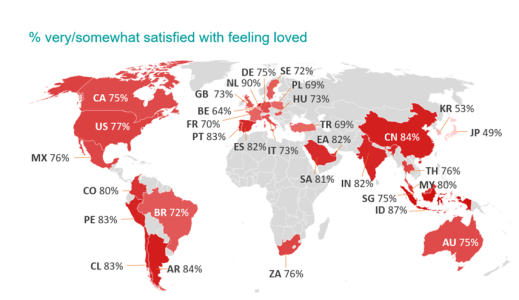
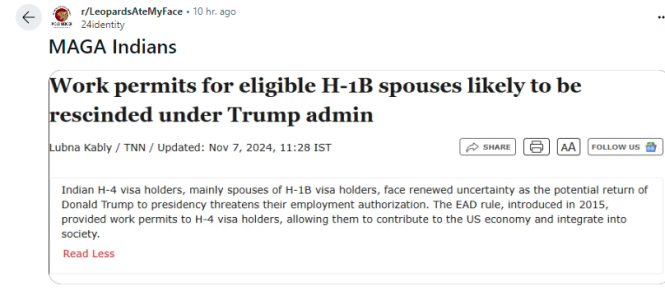
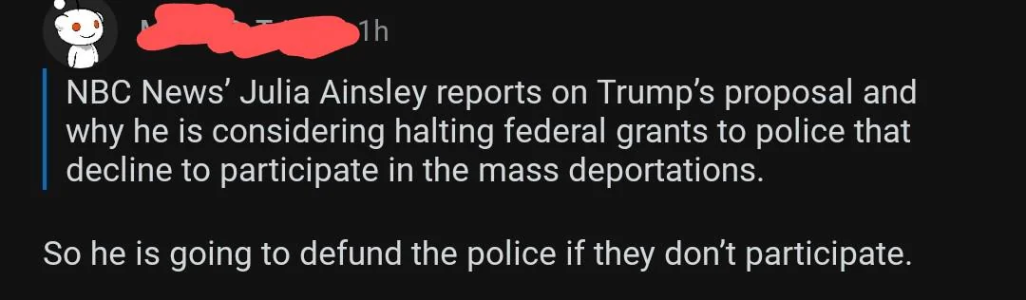
President Trump’s lawyer secretly obtained a restraining order last week to prevent a pornographic film star from speaking out about her alleged affair with Mr. Trump.
The White House’s spokeswoman, Sarah Huckabee Sanders, said on Wednesday that President Trump’s lawyer won an arbitration proceeding against the actress, Stephanie Clifford. She had been paid $130,000 shortly before the 2016 election in what she calls a “hush agreement.” But in recent weeks, she had
prepared to speak publicly about Mr. Trump, claiming his lawyer, Michael D. Cohen, had broken the agreement.
Ms. Sanders’s statement put the White House in the middle of a story that Mr. Trump and his lawyer had been trying to keep quiet for well over a year. The turn of events created the spectacle of a sitting president using legal maneuvers to avoid further scrutiny of particularly salacious accusations of an affair and a payoff involving the porn star, who goes by the name of Stormy Daniels.
Although Ms. Clifford said their relationship was consensual, the issue is particularly sensitive to Mr. Trump, whose campaign was dogged by allegations of groping and his boast of grabbing women’s crotches.
Ms. Clifford filed a lawsuit in Los Angeles Superior Court on Tuesday asserting that the nondisclosure agreement that accompanied the $130,000 payment was void because Mr. Trump never signed it.
Ms. Sanders said that the president had denied having an affair with Ms. Clifford or making the payment himself. She added that she was not aware of whether Mr. Trump knew about the payment to Ms. Clifford at the time.
“I’ve had conversations with the president about this,” Ms. Sanders said. “This case has already been won in arbitration, and there was no knowledge of any payments from the president, and he has denied all these allegations.”
Lawrence S. Rosen, a lawyer representing Mr. Cohen, said in a statement on Wednesday that an arbitrator “found that Ms. Clifford had violated the agreement” and barred her from filing her lawsuit.
Ms. Clifford’s lawyer, Michael Avenatti, said that he did not consider the restraining order, dated Feb. 27, valid and that she would proceed with her lawsuit in open court. “This should be decided publicly,” he said.